“A lock only keeps honest people out.”
With the current cybersecurity threat landscape, SMEs need to secure their organization to lower their exposure to risk. While there are a lot of tools available that are designed to mitigate or prevent threats, employing the proper framework and approach that aligns with your cybersecurity goals will make the most difference in your planning efforts.
Modern threats require modern approaches, and we can only prevent what we can anticipate. Because of this, it’s important to understand the difference between cybersecurity and cyber resilience so you can form your plan around both.
Let’s use home security as an example.
What is cybersecurity?
Cybersecurity is similar to employing basic security measures at your home – it’s preventative.
At your house, you might lock your doors, make sure your windows are closed before you leave, get a dog that barks, ensure the home is occupied by a sitter during vacations, and post signs outside stating you have cameras. These measures will be effective at keeping some people out.
Similarly, a cybersecurity strategy would include assessments and planning that best protect the organization from incoming attacks. This often refers to specific assets such as data, files, customer information, employee information, and information available via a cloud database or architecture. A strong cybersecurity plan will prioritize the most critical assets – pieces that are essential to keep operations running – as well as ensure there is a plan in place to protect them.
Proactive measures could include:
- Patch management: The process of upgrading or patching software to fix previous holes that posed security threats, adding features to make the software more secure, and fixing any bugs already present in the current version.
- Vulnerability management: The larger category surrounding patch management, vulnerability management includes finding and prioritizing vulnerabilities across architecture, as well as reporting found vulnerabilities and reconfiguring or patching where necessary.
- Assessing tools and technology: Looking at the tools and technology already in place can tell a seasoned cybersecurity professional a lot about where things are and what might need to be done to make systems more secure. They might examine firewalls, encryption tools, endpoint detection and response (EDR) software, antivirus software, spam filters, and anti-phishing tools, to name a few.
At the end of the day, the question you’re trying to answer with a cybersecurity plan is “What are we doing to protect the organization from incoming threats?”
What is cyber resilience?
Going back to our example of home security, bolting doors and windows is essential. However, locks can only prevent so much. As the saying goes, “A lock only keeps honest people out.” What happens when a burglar comes in through the window simply by smashing it? You may have slowed down an intrusion, but you weren’t able to prevent this incident. This is because you’re dealing with a burglar, a human who is great at adapting.
Cyber resilience acknowledges that not every threat can be prevented with cybersecurity measures because many attacks are also human-driven. It refers to an organization’s ability to mitigate damage and recover quickly in the event of a security compromise. In the case of homes, because we assume a thief can easily bypass controls like locks, we need to be able to detect them once they’ve entered the house and try to kick them out via motion sensors, cameras, alarms, and other reactive security measures. Cyber resilience is the organizational equivalent of those second-layer home controls.
Unlike cybersecurity, which focuses more on specific assets, cyber resilience takes a perspective that is generally organization-wide.
A cyber resilience plan will assess:
Department preparedness for security compromise
Which departments serve the most critical roles? During a crisis, it’s likely that keeping Finance and IT moving is more vital than making sure your marketing team is operational. Each department also contains its own risks regarding data loss that are inherent to the nature of work being conducted. For example, Finance will have financial data, Customer Support and HR could have personally identifiable information, and so on. Considering preparedness from these two angles – the critical role departments play in operations and the security considerations of the data they hold can help you better identify where to focus your efforts.
Threat Detection
Cybersecurity aims to prevent an attack but cyber resilience requires an organization to be able to detect a compromise and/or an intruder in your network. By knowing an attacker has made his way in (and finding out how), you’ll be able to take the appropriate action to flush the attacker out and protect your systems. Effective cyber resilience ensures your threat detection ability is on 24/7 as attacks can happen at any time.
Incident Response
Cyber resilience measures an ability to respond to any cyber incident — DDoS attacks, phishing, malware, and DNS tunneling, to name a few. For example, when it comes to ransomware reaction, the minutes matter. The longer a ransomware attack goes uninterrupted, the more files become encrypted, putting your organization at a greater risk of downtime or a complete shutdown. Ransomware attacks not only drain revenue, but they can poach irreplaceable data and erode trust with your customers and community. A rapid and appropriate reaction is key. This would include isolating infected data, reporting the incident to all critical departments (and potentially external parties), securing critical assets that may be at risk, and backing up files quickly and efficiently. Hesitation or gaps in protocol can be costly.
While ransomware has been a growing threat in recent years, other incidents also command attention. A robust cyber resilience plan would have a response to each scenario.
Post-breach recovery
After a data breach occurs, how will you respond? Business continuity plans lay out how operations will continue to move forward in the event of disruption. Do you need to shut down systems to protect data? Do you have a backup you can use to restore data and keep working? If so, what are your recovery point objectives (RPO) and recovery time objectives (RTO), and how can you make sure you meet them? A post-breach recovery assessment should consider all angles.
Internal / external communications
Because data breaches, ransomware, and other cyber incidents can reduce trust or create uncertainty, having the right internal and external communications plan is important for rebuilding that trust. Internally, your team needs to know who is responsible for what, and the steps that need to happen to ensure security and productivity. Externally, businesses should be forthcoming with clients, discussing what happened and what steps are being taken to remedy the situation. If there are any concerns about external data, they should be addressed in a timely manner, providing regular updates along the way.
What should an organization aim for?
Even though, at first glance, it may make sense to prioritize cybersecurity, doing so can actually create a false sense of…security.
Instead, aim for cyber resilience. Because it’s ongoing and always updating, prioritizing cyber resilience is a sign of maturity. Organizations need to be able to prepare for an inevitable scenario instead of naively hoping that what they haven’t prepared for won’t happen.
The NIST cybersecurity framework is a great place to start when looking towards a cyber resilience approach. Yes, cyber is full of inconsistency when it comes to terminology; but, rest assured, it’s focused on helping businesses become resilient. Doing it yourself takes a lot of effort and time. If you’re time and resource constrained, then a modern managed security service provider (MSSP) like SolCyber can help by offering cybersecurity management and monitoring services such as:
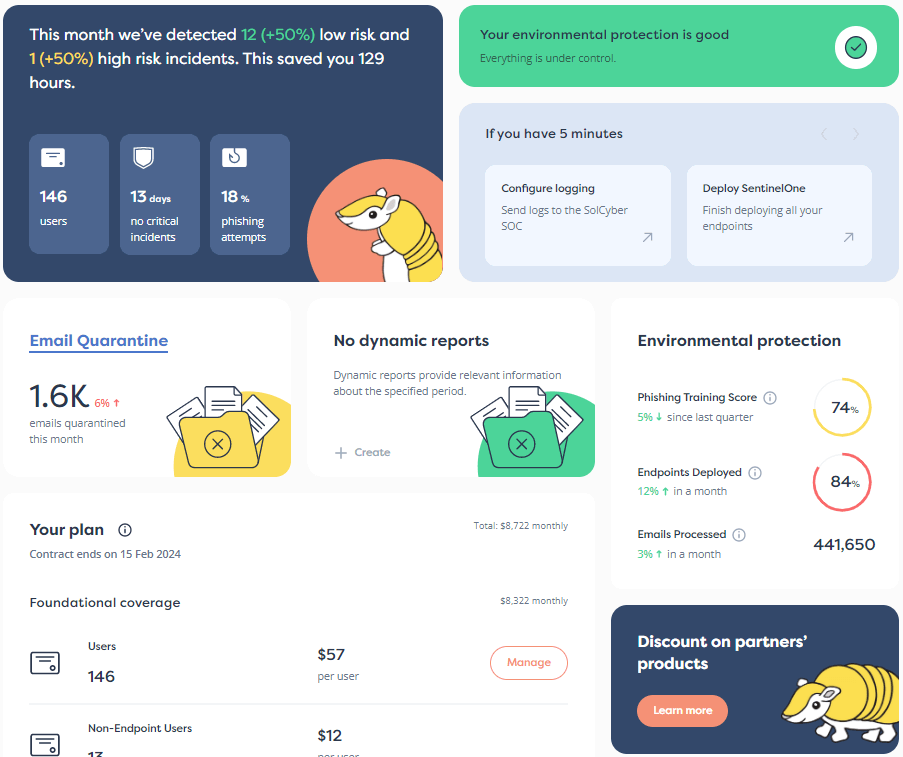
- Providing foundational security coverage using a leading tech stack that helps ensure resiliency.
- Offering ransomware assessment and training to ensure your systems and people are ready for an attack.
- Guaranteeing a secure outcome and giving you the right level of protection against breaches.
Ready for resiliency? Let’s talk.
FAQs
What is cybersecurity?
Cybersecurity serves as a preventative measure for your company, including planning and assessments that work to protect your organization’s critical assets from incoming attacks.
What is cyber resilience?
Cyber resilience acknowledges that not all organizational threats can be prevented, and focuses instead on mitigating damage and recovering quickly from security compromises.
Is cybersecurity or cyber resilience better for a company?
Both cybersecurity and cyber resilience should work in tandem to protect your company from threats. Think of them as a one-two punch.
Will cybersecurity prevent a data breach?
Cybersecurity can prevent many data breaches, but it can’t prevent attacks from threats it doesn’t yet know to expect. That’s where cyber resilience comes in.
Can cyber resilience protect me from a ransomware attack?
Cyber resilience works as a second layer of protection, getting your organization back up and running after a ransomware attack and filling in any gaps left by your cybersecurity plan.