- Solutions
- Foundational Coverage
An all-in-one security program that provides comprehensive protection for businesses of any size or maturity.
Advantages
Proactive Security, Efficient Approach, Value Beyond Security
Features
24/7 Level 2+ SOC Support, Proactive Posture Enhancement, Malware and Non-malware Response, Fully Curated Tech Stack, Live Security Training
Pricing
All-inclusive user-based subscription, includes software licenses
- MDR++
Begin your journey towards enhanced cybersecurity resilience with our fully managed detection and response services.
Advantages
Fast Start for Managed Detection & Response (MDR) and SIEM
Features
24/7 Level 2+ SOC Support, Live Security Training
Pricing
Based on the number of devices
- Security Monitoring
Experience better security monitoring, reimagined for the latest threats.
Advantages
24/7 monitoring and log ingestion delivers you round-the-clock security. We deliver actionable items based on our user-based analytics that enable you to quickly respond to events.
Features
Support for over 500 technologies, 1-year log retention, and advanced analytics including user behavioral analysis.
Pricing
$1000/month for 100 EPS (events per second).
- Extended Coverage
Add-ons that can enhance your protection or meet compliance requirements based on the specific needs of your organization.
Advantages
Flexibility to incorporate extra protection for different environments
Features
Cloud Visibility & Protection, Application Layer Encryption, API Protection and Visibility, Security Consulting and IR Retainers
Pricing
Incorporated into subscription payment
- Cyber Insurance+ Program
Your guaranteed path towards fast and affordable cyber insurance, available to all Foundational Coverage customers.
Advantages
Expedited Cyber Insurance Approvals, Significant Policy Discounts
Features
- Insurance provided by A+ AM Best rated insurance company
- Free access to cyber risk management platform
- Custom incident response vendors
- Foundational Coverage
- Who we help
- From Scratch
This service is tailored for companies seeking dependable security, streamlined implementation, and hassle-free progress, ideal for startups, SMBs, and growing organizations.

Simplify Complex Beginnings:
For companies that want security that they can depend on but don’t know where to start

All-Inclusive Cyber Resilience:
Super quick implementation – up and running in 30 days or less

Hassle-Free Security Journey:
For startups, SMBs, and organizations primed to see accelerated growth.
- Scaling Up
This service suits companies aiming to enhance existing cybersecurity, seamlessly integrate crucial tools, and achieve enterprise-level security and compliance.

Effortless Scaling:
For companies who have some cyber in place, but know they’ve got some gaps and want to upgrade ASAP

Streamlined Integration:
Seamlessly incorporate essential tools with Foundational Coverage and unlock dedicated security resources that deliver 24/7 management, detection, and response

Complete Assurance:
For organizations looking to win enterprise customers and meet compliance standards
- Overburdened
This service caters to companies seeking strategic efficiency, streamlined vendor management, and trusted support, particularly suited for enterprise organizations with established security frameworks.

Outsourced Expertise:
For companies who already have a solid security stack in place, but want to be more strategic and save time, money, and resources

Unburdened Focus:
Reduce the number of vendors you deal with to 1 and free up your current security resources to focus on what’s important

Trusted Support:
For enterprise organizations or those that already have a mature security posture, but need that extra support and expertise
- From Scratch
- Pricing
- Resources

Connect
-
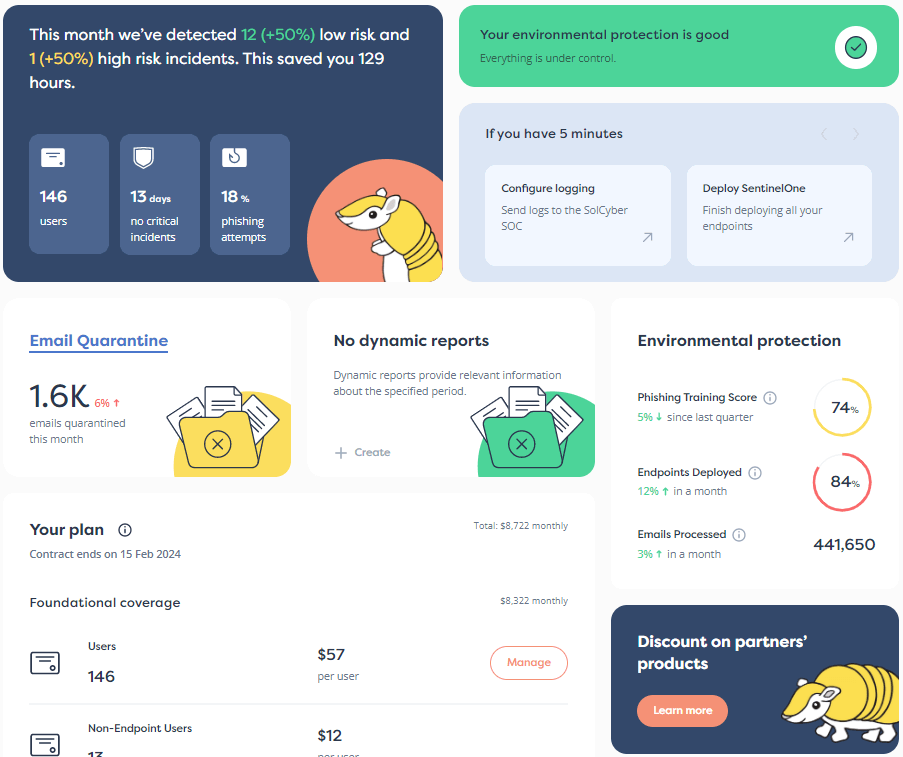
Customer portal
Check out a preview of our Customer Portal. It's actually GOOD.
-
About SolCyber
Who we are and what our mission is.
-
Careers
We want polite and caring people willing to tackle any problem and be part of something that’s, frankly, not the norm.
-
Partnerships
Find out about our "Howdy Partner" Program.
-
Contact
Contact us with any questions!
-
Customer portal

Learn
-
Case Studies
How we help clients achieve strong cyber resilience and peace of mind.
-
Blog
The latest cybersecurity trends and best practices from the SolCyber team.
-
Tales From An Armadillo
Series of true stories about our clients in comic format.
-
News
The latest cybersecurity news.
-
Downloads
Your go-to source for the latest SolCyber content: ebooks, infographics, datasheets, videos.
-
Case Studies
- Connect
- Learn