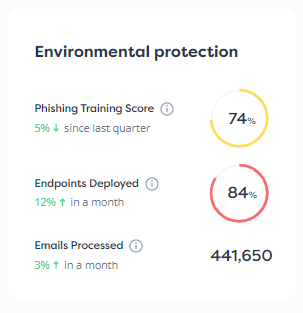
Traditionally, cybersecurity fell under the jurisdiction of IT, tech, or product teams and was overseen by the CISO. While these teams are still the primary players in cybersecurity decisions, the risk landscape is expanding, causing many companies to shift their thinking when it comes to cyber risk and cybersecurity. Because potential cyberattacks pose a larger risk to a business, the entire leadership team and the board (if it exists) should become key stakeholders over a business’ security efforts.
The person who will feel this responsibility shift most acutely is the CFO. Though CFOs have always been part of cybersecurity decision making, recent changes have pulled them in more deeply. It’s affecting more components of their role, so they are becoming far more influential in the cybersecurity decision-making process.
Here, we’ll cover why CFOs should be more involved in decisions related to a business’ cybersecurity practices, what they should consider when making security investments and how they can provide more value to their security counterparts.
Cyberattacks are creating greater impacts on businesses
As people become increasingly reliant on mobile devices, applications, IoT devices, and computers, more sensitive data belonging to an organization is being shared online than ever before. And as more people work from home, this data is passing through less secure networks. Both of these trends provide bad actors with more opportunities for hacking and entering an organization’s network.
In addition to the number of attacks increasing, the techniques hackers are using is expanding as well. Malware and DDoS attacks that were once easy to recover from are being replaced with sophisticated ransomware and phishing attacks that pose greater risks to a business. Compromises are becoming more severe and the consequences more dire.
Cyberattacks are no longer incidents where a server may come down for a few hours. It may be the difference between your organization being able to continue its normal business processes versus paying a large ransomware payment your organization would never find acceptable.
Beyond the loss of data, the risk of a breach includes a number of other risks and costs, including:
- Financial risk: According to the Ponemon Institute and IBM’s the 2021 Cost of Data Breach report, data breaches in 2021 cost companies an average of $4.24 million. That includes a variety of costs, including ransomware payments, data loss costs, remediation costs, and legal fees.
- Reputational risk: Companies are required by law to report on any data breaches they experience, and that nearly always results in reputational damage. When you lose a customer’s trust, you lose their business. PCI Pal reports that 62% of Americans claimed they would stop buying from a brand for several months following an attack. And an Aon Global Risk Management survey found that some companies have seen a 25% drop in market value in the year following a cyber attack.
- Compliance and legal risk: When a breach involves customer data, which is often, a lawsuit is virtually a given. That means your company is on the hook for legal fees and settlements such as paying for affected consumers’ credit monitoring and identity theft protection. You may also need to pay fines if an investigation determines that you didn’t meet regulations such as GDPR, HIPAA or CCPA.
- Operational risk: If your business is hit with a ransomware attack that locks up your network, you won’t be able to serve customers until the issue is resolved, which could take hours, days, or even weeks. In that time, you’re losing business and profits, which only adds to your financial losses.
Because there are so many risks and costs associated with a data breach, companies like Forbes and American Express are ranking cyberattacks as one of the top risks businesses face today. Because this risk affects so many areas of the business and has so many associated costs, CFOs need to become more involved in their organization’s cybersecurity efforts.
There are significant financial considerations when it comes to security
While IT and security teams may provide technical recommendations needed to protect your organization, it’s typically up to the CFO to approve those costs. If a CFO doesn’t understand the risk and associated costs of a cyberattack, security efforts might not be prioritized in the way they should be. It’s important for CFOs — and other stakeholders — to view cybersecurity efforts through an opportunity cost lens.
Failing to properly secure your environment can result in a multi-million-dollar breach that has lasting effects on your ability to make money and grow to serve your customers. But that’s not the only cost associated with delaying security implementation. By deprioritizing cybersecurity, you’re also racking up cyber debt.
Much like technical debt, cyber debt accumulates when you fail to implement appropriate security controls early on and instead opt for a patchwork cybersecurity strategy. As your business grows, so do the gaps, leaving you more and more vulnerable. By the time you get around to closing the gaps and rethinking your security strategy, it becomes a colossal — and costly — effort.
Though security technology, MSSP and EDR services, and cyber insurance can look like tools that incur significant costs, CFOs should look at these expenses as investments that will save you crucial dollars in the long run. Cyber debt needs to be eliminated sooner or later. By investing in these tools early, you’ll significantly reduce your cyber debt risks, reduce the risk of experiencing a costly breach, reduce your overall attack surface, and have the tools in place to safely scale your operations and attract potential investors and partners.
CFOs should help establish and enforce cybersecurity policies
Procuring the appropriate tools and selecting security vendors are just a first step of an effective security strategy. You also need to establish internal cybersecurity policies and procedures. While your security team can develop the appropriate protocols, they’ll need the help of the CFO and leadership team in enforcing them.
A number of cyberattacks rely on social engineering, preying on human error and innocent ignorance. Even the best email protection software can’t stop an employee from opening a malicious attachment, and no amount of security tools can keep your employees from oversharing documents or providing too many people with admin access. These costly mistakes need to be controlled with policy, training, and enforcement.
The CFO should work with the CIO or CISO to justify, establish and enforce policies and processes that encourage employees to follow security best practices. The earlier you can do that, the better, so you’re not facing employee resistance or trying to break bad habits that have formed over the years. Establishing these processes early on is key to creating a secure environment and maintaining resiliency as new software, devices, and employees are added.
When bringing on new tools or security partners, a CFO can also be responsible to make sure any cyber protections and added layers of security are comprehensive enough to actually make a difference in an organization’s security posture. This includes device, network, and environment coverage, ensuring detection and response capabilities are improved, and reducing an organization’s overall risk of a breach.
Though cybersecurity strategy is often led by the CISO, small and midsize businesses that lack that role might rely more heavily on the CFO to own security and business decisions. If you need to outsource or supplement your existing security with external expertise, you’ll need the help of an MSSP.
SolCyber helps companies make smart security investments, so your organization gets foundational coverage without overpaying for services you don’t need. We not only help you secure a tech stack, but we offer around-the-clock monitoring and detection as well as expertise on how to set up a secure environment. Contact SolCyber to learn more about how we can help your organization invest in a safe future.