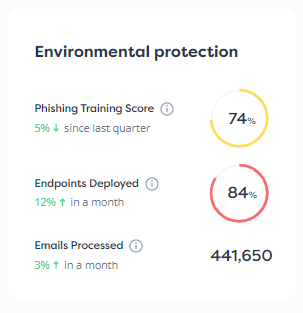
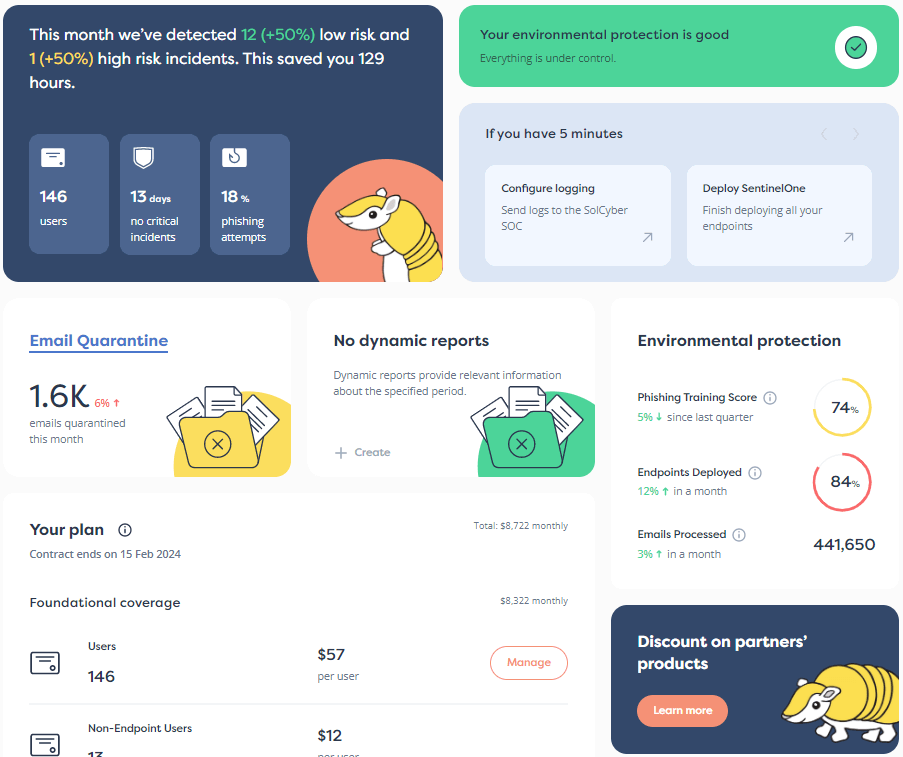
3 key questions to ask yourself to evaluate your cybersecurity preparedness.
The cybersecurity landscape changes fast, and in 2023 we’re seeing shifts at a faster clip than ever before. We’re likely to see continuing increased attacks on the supply chain, threats to critical infrastructure, a rise in ransomware, and pros and cons arising from the proliferation of artificial intelligence. Economic uncertainty, continued remote work trends, and skill shortages will be some of the major contributing factors to this landscape.
Threats evolve and change, company risks are always shifting, and new technology is constantly coming out. So, how can organizations keep up with it all, know how to adapt properly, and ensure they’re focusing on the right things?
Your organization can not only keep up but stay ahead of looming threats by asking the right questions and shifting your strategy accordingly. Start 2023 off right by asking yourself the following questions:
1. When was the last time you updated your cybersecurity?
What worked for your organization 10 years ago, or even 5 years ago, isn’t going to work the same way now. The pandemic changed work practices and remote working prevalence dramatically: Before COVID-19, only about 6% of employees worked remotely. Now, almost 15% of all high-paying jobs are remote; and it’s expected that by 2025, 22% of the American workforce will be remote.
While this is seen as a positive by many employees and employers, there’s also a downside – remote work environments come with increased cybersecurity risks. Unless the proper safeguards are in place, hybrid and remote environments create larger potential attack surfaces and unique vulnerabilities not seen in non-remote environments.
If your organization invested in basic security tools like antivirus and firewalls years ago without updating anything recently, you’re not addressing the risks that matter today (and will matter even more in the future). Many cybercrime tactics can evade basic security measures. Social engineering attacks, sophisticated ransomware, and attackers that find back doors to your systems can cause problems if you’re not regularly evaluating and updating your cybersecurity practices.
The rise in remote work isn’t the only area that’s created new vulnerabilities. Here are some other considerations security leaders need to be aware of:
- The use of the cloud (via cloud-based third-parties, SaaS apps, and more) has increased the speed and agility of business but has also created an entirely new vector and potential attack surface that needs to be secure.
- Are you using software that could let attackers in? Supply chain risk is not just something that happens in the movies. It’s an area that is being targeted with more and more fervor, increasing 600% in the last few years!
- Single sign-on and SaaS applications have increased productivity, but the downside is that stolen credentials can be more easily abused.
If you’re not privy to the latest threats, you are placing yourself in a vulnerable position. Look for ways to modernize your cybersecurity strategy and tech stack by adding or replacing current tools. And, if you don’t know what threats are most urgent to address, keep reading!
2. Is your cybersecurity equipped to handle modern threats and risks?
It’s important to state from the outset that attackers don’t discriminate based on the size of a company. That means you won’t necessarily fly under the radar simply because you’re a startup or small business. In fact, almost half of all cyber breaches and 82% of ransomware attacks have happened at businesses with fewer than 1,000 employees. With that in mind, consider the risks and threats virtually all organizations face today and consider your preparedness in light of the following:
- Ransomware: Ransomware is generally spread through phishing emails. When a recipient downloads a malicious file, it starts encrypting all files, holding data hostage until the criminals receive a ransom payment. Recently, ransomware has expanded with the growth of ransomware as a service (RaaS), attacks on the supply chain, and double extortion tactics, where ransomware attackers demand payment to keep from leaking information. In 2022, ransomware was involved in a quarter of all breaches.
- BEC: Business email compromise (BEC) attacks trick users to pay fraudulent accounts by impersonating key business partners or even the CEO. Without the proper tools, such as advanced email security that can uncover sophisticated BEC attacks, this type of assault is difficult to detect as it contains no malware.
- Cloud-based attacks: As remote working has become more common, organizations are sharing more data in the cloud, making it a more appealing venue for attackers to take over through methods like brute force attacks, social engineering, or exploiting known vulnerabilities within cloud frameworks. Almost half (45%) of all attacks were cloud-based in 2022, and one big culprit for vulnerability comes from cloud misconfiguration, which accounted for 15% of all breaches. As companies rely more on cloud technologies, we can expect to see this trend not only continue, but accelerate.
- Third-party attacks: Sometimes a threat doesn’t start with your business; instead it originates from a third-party vulnerability, such as an organization that’s part of your supply chain. Software vulnerabilities from third-parties were the initial attack vector for 13% of all data breaches in 2022.
- Account takeover attacks: Using stolen credentials, cybercriminals can take over an account (which can often come from users having similar or identical credentials across multiple accounts) and infiltrate your organization. In 2022, stolen or compromised credentials were the most common initial attack vector for businesses experiencing a data breach.
Evaluating your cybersecurity stance in 2023 should involve asking yourself whether your department is able to detect, manage, and respond to these trending attacks. Previously, threats to security predominantly involved malware; but, in recent years, the cybercrime landscape has become much more intricate. Knowing that criminals are focused on attacking people means you have to be mindful of the tools you have in place and offer the training necessary to keep team members on their toes.
Despite the best laid plans, vulnerabilities can arise from small security cracks that form over time. For example, insecure passwords that were revealed in other data breaches, leaks and exposures from misconfigured systems, or failure to meet the newest data compliance standards. These weaknesses can creep up on your business and cause major consequences. Consider your gaps in risks and resources. What tools and services do you need to add to defend against 2023’s most prevalent threats?
Of course, even if you can make a list of cybersecurity priorities based on what has the most room for improvement, it doesn’t mean you’ll have the resources to pull it off. Talent shortages and tight budgets can make it difficult to expand your IT department.
3. Do you need a cybersecurity partner?
If these questions leave you feeling overwhelmed by how much ground needs to be covered, you’re not alone. An unfortunate reality of today’s cybersecurity landscape is that it’s more likely than ever for organizations of all sizes to be breached or attacked. Your best bet is to be prepared and try to minimize and offset the damage as much as possible.
However, few companies have the resources to manage this kind of coverage 24/7, and even fewer have teams that are the right size with the right training to perform everything that’s needed to stay on top of trending threats. With the current cybersecurity workforce gap at around 3.4 million, internal resources can be expensive, difficult to hire, and even harder to maintain.
Rather than trying to navigate those choppy waters alone, it might be smart to partner with key service providers. This includes managed service providers, cyber insurance companies, and providers offering incident response retainers.
Managed Services
Whether an organization opts for MDR or MSSP services or both, having a program in place to detect threats and take action is important for a business of any size. But if you happen to be a small business or a startup, look for a modern managed security provider like SolCyber that’s made for smaller organizations which may not have a robust security team or fully built-out tech stack.
Cyber Insurance
Cyber insurance companies can help protect organizations by offsetting the financial risks from cyber attacks. However, in order to be covered, organizations have to meet certain requirements, which can include mandatory cybersecurity preparedness training, 24/7 monitoring and response services, offsite backups, timely critical vulnerability patching, and more.
In 2023, cyber insurers are becoming more sophisticated. Meeting their standards is worth your time because it means you’ve taken steps to protect your business that many others have not. Meanwhile, cyber insurers are working to develop requirements based on ransomware as a service, increased social engineering attacks, and any other threats on the horizon.
Incident Response Retainer
Should an incident occur, your organization needs to have response plans in place. An incident response retainer can help you respond quickly and properly to an incoming threat or attack.
How you prepare, detect, analyze, contain, remove, and recover from an event can be provided by a security partner.
Downtime can mean loss of revenue as well as negative impacts on your reputation, workforce, and client relationships. Because you can’t protect your business from every potential threat, having a plan for how to contain and respond to incidents is vital to your business continuity.
Consider SolCyber
SolCyber provides fully managed 24/7 detection, response, and cybersecurity support to organizations looking to improve their cybersecurity posture and preparedness. Built with modern threats in mind, our services provide a comprehensive solution that meets key cybersecurity requirements. SolCyber can help you monitor essential elements of your environment and respond accordingly when a threat is detected.
Our tech stack is designed to fight modern threats. Whether you’re looking for just the basics or extended coverage, SolCyber’s curated technologies offer endpoint detection and response, advanced email protection, cloud protection and visibility, security consulting, and more. To provide even more comprehensive cybersecurity resilience, we’ve partnered with Surefire Cyber to provide incident response services and with Converge for cyber insurance.
Ready to take on 2023 challenges without breaking a sweat? Contact us today!