Cybersecurity in the manufacturing industry is not a new topic, but it is an increasingly important one. Like many other industries, manufacturing is rapidly adopting new technology, which is widening the threat landscape. Unlike other industries, most of this new technology falls under the umbrella of operational technology (OT) rather than information technology (IT). OT is a combination of hardware and software that manages industrial operations. It includes (among other things) industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems which tend to be the target of manufacturing cyberattacks.
In the first nine months of 2021, reconnaissance of internet-connected SCADA networked devices and sensors increased by 2,204% according to IBM’s 2022 X-Force Threat Intelligence Index. The same report indicated that manufacturing was the most attacked industry, accounting for 23.2% of all attacks.
Attacks on OT can disrupt or completely shut down operations of a manufacturing facility, result in stolen intellectual property; and, in the most extreme cases, result in loss of life. Not to mention that the lost revenue, financial impact, and reputation damage of a cyberattack are enough to put many manufacturers out of business. Given those factors, now is the time to take a serious look at your business’s security posture.
Why is manufacturing the most attacked industry?
The answer to this question is a complex one and includes a unique combination of elements. While financial institutions and large corporations may seem like more practical targets for bad actors, attacks on the manufacturing industry are actually rather lucrative.
- Time is money: There are few industries where this concept rings more true than manufacturing. A disruption to production lines caused by a cyberattack could cost thousands of dollars per minute. That means manufacturers are quick to pay ransoms to get their lines back up and running.
- Trade secrets are valuable: The manufacturing industry is highly competitive, especially when it comes to foreign entities. Whether the goal is to ask for a ransom or sell trade secrets on the black market, intellectual property theft is reported as one of the most costly cyber threats in the manufacturing industry.
- The industry is vulnerable: Finally, the manufacturing industry is targeted so often for the simple reason that most companies are not equipped to defend themselves against a breach. The industry is undergoing mass digitization and the appropriate security measures are, by and large, not being implemented, leaving the industry open to attack.
Why the manufacturing industry remains vulnerable
Not only does the manufacturing industry provide inherent value to hackers, but it’s also fairly easy to infiltrate — especially right now. Though there are many reasons for this, topping the list is the mass move to smart factories.
- The emergence of smart factories: In an effort to maximize productivity, eliminate inefficiencies, and cut costs, factories across the country are investing in smart technology like AI and automation. Manufacturers are adding sensors left and right as well as new endpoints like IoT devices. While these new devices can help cut downtime, optimize production lines, and keep machinery functioning with predictive maintenance, they also open up the attack surface for bad actors. In fact, 61% of intrusion and breach incidents occur at OT-based manufacturers.
- The divide between OT and IT: The move to smart factories is ultimately a positive decision for manufacturers, but manufacturers need to rethink the way they are updating their equipment. Right now, many OT purchases are made by factory-floor operations leaders. IT is being left out, and therefore can’t complete the necessary due diligence to ensure new equipment is the best option from a security standpoint, which is especially important given the newness of the technology. For example, the Cybersecurity and Infrastructure Security Agency (CISA) lists 1,200+ known OT system-related security issues, vulnerabilities, and exploits from more than 300 OEMs and system providers. Complicating matters further, IT leaders also need to ensure any new technology, once procured, is incorporated into the company’s network in a safe way.
- Equipment isn’t built with security in mind: Many IoT devices and smart equipment on the factory floor lack the same cybersecurity capabilities as IT devices. These devices were built more for efficient real-time data transfers and reporting than for security. So IT professionals need to take extra care in securing these devices to ensure the data is protected while it’s stored on the device or being sent from the device to another destination over the network.
- Inability to patch OT: Unlike IT, OT is built to last for decades. While that’s a compelling selling point for someone considering such a large purchase, it means that this equipment is eventually running on very old, often unsupported, software and firmware. Unfortunately, the way these systems are built doesn’t allow them to be updated and patched, which leaves them vulnerable to attack. As new threats emerge, there’s no means of updating the software to protect against those new threats.
- Manufacturers rely on dated security practices: Manufacturers tend to adopt lean practices, and building an in-house security department hasn’t typically been a priority. So many manufacturers are relying on dated security practices like legacy perimeter networks and air-gapped computers that ultimately won’t secure their operations in today’s high-tech, connected, and cloud-based environment. As more devices — and more types of devices — enter the environment, internal resources don’t know what steps to take to secure them.
Combining old software and old practices with new technology is a recipe for disaster. That makes it essential for manufacturers to look at security more holistically and make it a priority moving forward.
What manufacturers can do to secure their environment
Because the industry is in the midst of massive technological updates, now is the time to invest in cybersecurity. Each new technology added to the production floor should be secured as it’s being installed, and IT should be involved in the procurement of all devices and software. This will ensure that as a company grows, it grows safely. In addition to a company-wide commitment to security, manufacturers should take a few steps to secure their production lines.
- Conduct a risk assessment: The best way to close any gaps in your security posture is to know where they are. Conduct an annual risk assessment to ensure appropriate defenses are in place and identify where work needs to be done. Annual risk assessments are also typically a requirement for cyber insurance, which comes next.
- Buy cyber insurance: Regardless of the industry, businesses need cyber insurance. Should a breach occur, cyber insurance minimizes the massive costs a company would face and decreases the chances of going out of business.
- Build an incident response plan: Although manufacturers don’t want to think about forced downtime, they need to be prepared for it to happen. An incident response plan lays out what needs to be done in the event of a breach as well as who is responsible for each task to ensure your line is back up and running as quickly as possible.
- Invest in a zero-trust network access framework: The zero-trust principle essentially states that no user or device is automatically trusted and therefore needs to be verified. Authentication and authorization of both the user and the device are necessary in order to access a company’s network, software, or applications. Given the number of shift workers in factories and warehouses, IT managers should also be cautious about who is given access to privileged accounts. Equipment logs should be tracked carefully, and each individual user should only have access to the systems and data necessary to do his or her job.
- Secure your OT and IT with the right tools: Businesses large and small need to invest in the cybersecurity basics, but manufacturers need to ensure they have the right tools to cover both IT and OT. And, because a very specific strategy is needed to secure OT, they must also make sure to choose a security partner with experience in the industry.
- Train your staff: Unfortunately, most security breaches are a result of human error, so even the best technology won’t completely protect manufacturers. Cybersecurity training should be hosted regularly and cover common attacks and best practices for using the technology on the factory floor. Because the industry is still relying on dated defense tactics, make sure your teams understand which security tactics are effective and which are unreliable.
If your company is like most manufacturers, you don’t have — and can’t invest in — an in-house cybersecurity team, so you’ll need to outsource many of your security efforts to an outside vendor. You need an experienced partner who can provide 24/7 monitoring and response services. In an ideal world, that partner would also provide the necessary tools and technology to secure your production floor.
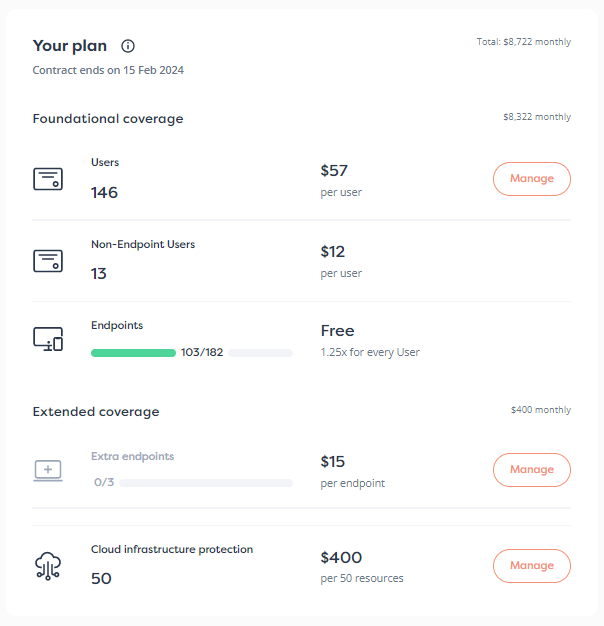
SolCyber has been helping manufacturers secure their OT and IT, so they can rest assured their production lines won’t be disrupted. Our Foundational Coverage ensures small to mid-sized manufacturers have everything they need and nothing they don’t. (We can also get you up and running in days because we too understand that time is money.)
Ready to secure your production line? Reach out to SolCyber, the experts in cybersecurity, to see how we can help.
Follow us on these social platforms!
LinkedIn: https://www.linkedin.com/company/solcyber-managed-security-services/
Twitter: https://twitter.com/SolCyberMSS
Facebook: https://www.facebook.com/solcybermssp
Instagram: https://www.instagram.com/solcyber_mssp/