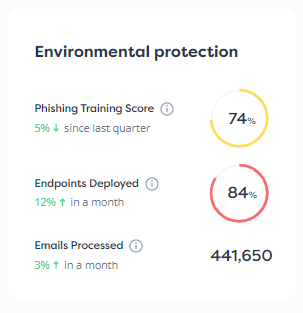
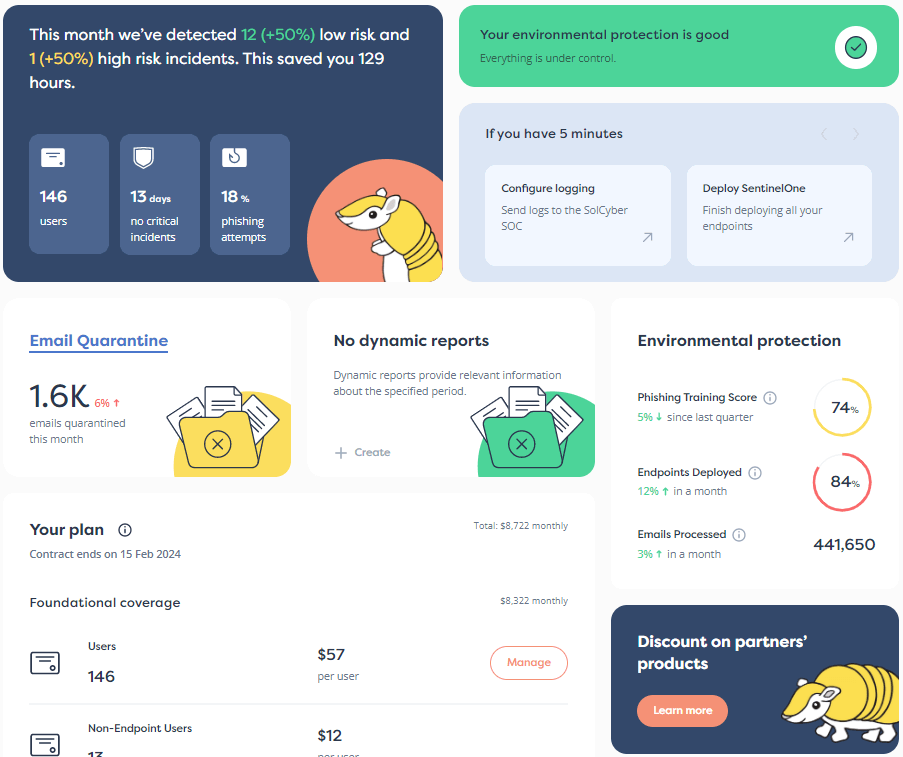
A swift and adequate response to an active cybersecurity threat can mean the difference between your company surviving the incident or going under. Small to mid-sized enterprises (SMEs) are especially at risk because they are looked upon as low-hanging fruit by hackers and they tend to have fewer defense and response mechanisms in place than larger corporations, especially because of budget constraints.
According to IBM’s Cost of a Data Breach Report for 2021, the average cost of a breach was over $1.2 million higher when the data breach lifecycle was longer than 200 days. In other words, the longer the attack remains unresolved, the more expensive it becomes. These costs range from direct costs associated with handling the attack itself, to regulatory fines.
In this article, we’re going to look at what Incident Response (IR) comprises of, what is required for an effective IR plan, and the most cost-effective way for an SME to implement an IR plan.
What is an IR plan?
An Incident Response plan is exactly what it sounds like — the precise steps required to contain and recover from a breach.
Above all else, an IR plan needs to be actionable. No one is going to break the glass to read an IR plan that is 100 pages long.
If there are more details to a certain step of an IR plan, those details should be written in a separate playbook. But it’s important to note that the playbook itself should also not be a lengthy tome of minute details that no one will read. A playbook should cover the overall guidelines, roles, and responsibilities of mitigating a specific facet of a larger risk, such as ransomware for example. The IR plan can then refer to these playbooks at specific steps.
An IR plan and each playbook should spur action.
The IR playbooks should cover both technical and non-technical aspects of the response plan. Non-technical aspects should include roles and responsibilities, contact lists for stakeholders, and outlines for communication plans.
The IR plan itself should also cover other key elements such as:
- Who declares an incident, and how is it done?
- What are the roles and responsibilities associated with the plan?
- Is the compromise a low-impact or high-impact incident?
- How does the severity of the incident affect the type of team that will deal with it?
- What are the general containment and investigatory steps?
- Who are the internal and external stakeholders involved and how do you involve them?
The playbooks would then go into more granular steps, often separated by roles.
The type of attack would also define the types of steps that need to be taken, and playbooks are usually tailored to those.
Expected outcome
The expected outcomes of an IR plan are:
- The attacker and threat are swiftly contained and removed.
- An analysis reveals the vulnerability, path of the compromise, and overall impact of the incident.
- Post-incident remediation fixes are implemented so that the vulnerability is closed and future attacks through that vector do not recur.
- Communications to relevant stakeholders including the board, customers and even the authorities are sent out.
Why is an IR plan needed?
The beginning of an incident is always chaotic. The purpose of an IR plan is to reduce that chaos as much as possible, as well as the pain involved in resolving the problem.
Having the right IR plan in place that people are familiar with and is well exercised enables the team to remain calm and to quickly take action. This results in less business interruption and overall lower costs.
An incident response will depend very much on the type of attack. Low-impact attacks are far easier to address than high-impact ones, such as ransomware.
In a ransomware attack, speed of action is absolutely vital. The faster the overall systems can be protected or restored, the lower the chances of business interruption or a ransom payout.
Ransomware attacks have spiked in recent years, making the need for IR plans even more vital because of this type of attack’s immense potential for damage.
Is IR just for large companies and enterprises?
Small businesses are prime targets for cyberattacks because they typically have a high hit rate. A cybercriminal that penetrates just 10% of 1,000 attack attempts on SMEs will likely be more profitable than one that penetrates 1% of attack attempts on Fortune 500 companies. Attacks against SME’s also allow threat actors to largely stay under the radar, avoiding uncomfortable scrutiny from law enforcement (Think back to the famous Colonial Pipeline breach. That was a mistake on the threat actor part!).
According to Verizon’s 2022 Data Breach Investigations Report, most attacks occur only in a handful of steps such as (1) a phishing email is sent, (2) the user clicks a download link, and (3) ransomware is installed. “Our job as defenders is to lengthen that attack path,” the report says. “Attackers tend to avoid longer attack chains because every additional step is a chance for the defender to prevent, detect, respond to and recover from the breach.”
Large companies with a robust security posture — and therefore longer attack chains — provide hackers with fewer opportunities to penetrate their systems.
SMEs also struggle because they are extremely understaffed and often have very limited investment into security technologies, opening the door to a severe type of attack called an Advanced Persistent Threat (APT). This type of attack is when an attacker uses sophisticated methods to ensconce themselves within a computer system and carry out a lengthy attack that lasts as long as the attacker is not detected.
The effects of an APT can be devastating, such as was the case in the six-month-long breach at AMCA, a healthcare billing provider, that resulted in tens of lawsuits being filed and the theft of the private health information of over 20 million Americans.
Cybercriminals are opportunistic and SMEs provide the largest opportunities. We have seen a decline in the focus on large companies recently. Larger companies are becoming more prepared which greatly reduces the chances of a successful attack on them.
In-house versus external IR response teams
An external IR provider can create a thorough and comprehensive IR plan for a small business in just a few weeks. Larger corporations with thousands of employees and branches across the globe may need a couple or three months for an IR plan.
The broad-level steps of an IR plan are essentially the same for both large and small companies, but larger companies require a higher level of detail to answer more complex questions.
An in-house IR plan only works if you have a robust security and IT team in place. This is normally out of the reach of most SMEs due to the immense costs involved in putting together and maintaining such a team.
Other experts required in an IR plan
While the attack is technically focused, a successful breach often implicates multiple aspects and departments within the business. It’s important as part of the IR plan to include other stakeholders or expertise outside of IT. This could include:
- Legal counsel that is expert on privacy regulations. This is unlikely to be in-house counsel due to the level of expertise needed.
- An expert social media PR team will also be required to field any backlash after announcing the attack which, in many jurisdictions, is required by law depending on the type of data that was compromised.
- If you have cyber insurance, your cyber insurance representative should also be involved to begin the claims process immediately.
It all comes down to immense expertise which is itself highly costly to maintain at an in-house level but can be outsourced quite easily with the right partner.
How an IR company can help
An external IR company can help SMEs respond swiftly to incidents by bringing in the necessary expertise required to guide best practices in handling incidents. Companies specializing in IR are available 24/7 when an attack occurs, applying the highest-grade technology to close the attack and then recover from it.
An IR company will take care of preparing the IR response plan along with creating the associated playbooks that cover the most impactful risks. If such documentation already exists, the IR company will overhaul that documentation to ensure it is aligned with best practices. Furthermore, they often include tabletop exercises to test out the plan so everyone is well prepared for a breach attack.
Above all else, the IR company will make sure that the documentation is actionable.
SolCyber has teamed up with IR experts Surefire Cyber to provide all our clients with the necessary IR plan and support required in the unlikely event that they are attacked. By partnering up with a reliable partner such as Surefire Cyber, SolCyber can provide a turnkey security solution to all SMEs, covering every possible aspect of security from beginning to end.
Click here to learn more about how SolCyber can help your SME ramp up its security posture without breaking the bank.